New Vendor Email Compromise Attack Seeks $36 Million
The new season is a great reason to make and keep resolutions. Whether it’s eating right or cleaning out the garage, here are some tips for making and keeping resolutions.
The details in this thwarted VEC attack demonstrate how the use of just a few key details can both establish credibility and indicate the entire thing is a scam.
It’s not every day you hear about a purely social engineering-based scam taking place that is looking to run away with tens of millions of dollars. But, according to security researchers at Abnormal Security, cybercriminals are becoming brazen and are taking their shots at very large prizes.
This attack begins with a case of VEC – where a domain is impersonated. In the case of this attack, the impersonated vendor’s domain (which had a .com top level domain) was replaced with a matching .cam domain (.cam domains are supposedly used for photography enthusiasts, but there’s the now-obvious problem with it looking very much like .com to the cursory glance).
The email attaches a legitimate-looking payoff letter complete with loan details:
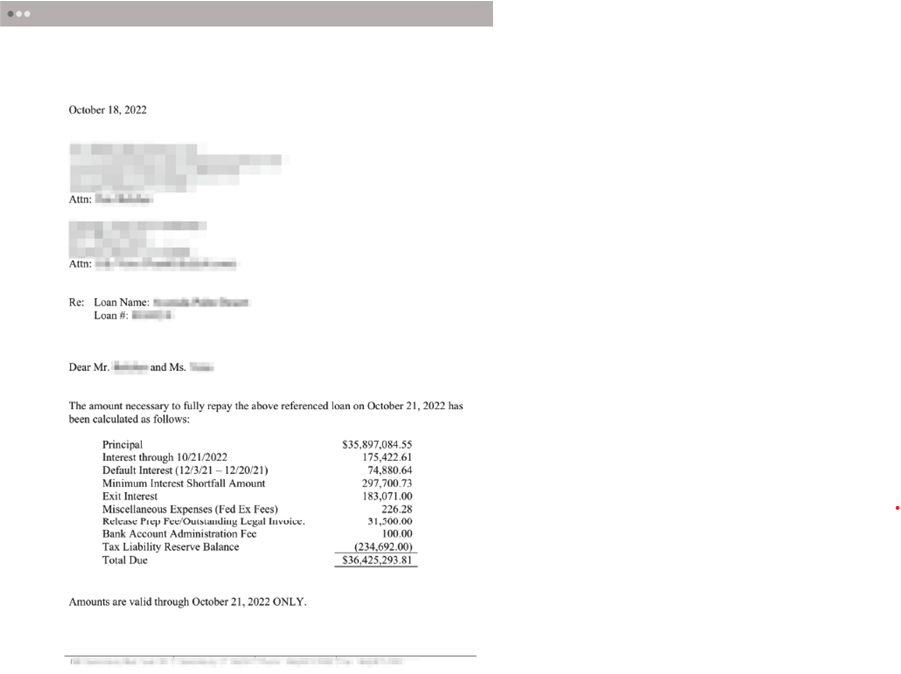
According to Abnormal Security, nearly every aspect of the request looked legitimate. The telltale signs primarily revolved around the use of the lookalike domain, but there were other grammatical mistakes (that can easily be addressed by using an online grammar service or ChatGPT).
This attack was identified well before it caused any damage, but the social engineering tactics leveraged were nearly enough to make this attack successful. Security solutions will help stop most attacks, but for those that make it past scanners, the user needs to play a role in spotting and stopping BEC, VEC and phishing attacks themselves – something taught through continual Security Awareness Training.
Source: Abnormal Security, KnoweBe4 Cyberheist Blog















